
Vulnerability Management with ThreatMate
Continuously protect your external and internal assets from known threats. ThreatMate’s Vulnerability Management solution automatically discovers exposed services and identifies weaknesses—so you can fix them before attackers do. With daily external scans and twice-a-day internal checks, ThreatMate empowers you to stay on top of new vulnerabilities in real time.
How ThreatMate’s Vulnerability Management Works
Continuous Scanning
-
External Assets (Daily): ThreatMate runs daily scans against your public-facing infrastructure—domain names, subdomains and IP addresses—ensuring that any newly discovered exposure is reported quickly.
-
Internal Assets (Every 12 Hours): ThreatMate’s Unified Agent continually checks your network devices behind the firewall, performing vulnerability scans twice a day to uncover anything from unpatched workstations to misconfigured servers.
Comprehensive Port & Service Discovery
-
Full TCP & UDP Coverage: ThreatMate enumerates all open ports, investigating both TCP and UDP services.
-
Service Fingerprinting: Our system identifies each running service (e.g., HTTP, SSH, SQL) and checks it against the latest known vulnerabilities, ensuring no hidden exposures remain out of sight.
Intelligent Prioritization
-
CVSS & EPSS Scores: ThreatMate doesn’t only rank issues by severity; it also factors in Exploit Prediction Scoring System (EPSS) data to highlight which vulnerabilities attackers are most likely to target.
-
Mission Plan Integration: All discovered vulnerabilities flow into your unified mission plan, displaying clear, prioritized fixes.

Rapid Remediation & Alerting
Findings & Alerts
Each vulnerability triggers an in-platform alert that you can acknowledge or remediate.
ThreatMate can send email notifications the moment a high-risk exposure is found.
Granular Control
Mark vulnerabilities as addressed or escalate them in your workflow.
Ensure your team has a real-time view of critical issues that need immediate attention.
Automatic Updates
ThreatMate’s vulnerability definitions refresh daily, so the system stays current with the latest threats.
Generative AI Solutions
Speed up remediation with AI-generated fixes for every discovered vulnerability. Instead of spending hours researching individual exploits, your team instantly receives tailored solutions powered by generative AI—helping them resolve issues faster and focus on higher-level tasks.


External Vulnerability Management Highlights
Safe & Adaptable Scans
ThreatMate scans sensitive firewalls in a slow and cautious manner to avoid triggering port scan protections.
Exposed Service Detection
Identifies risky protocols like Telnet, FTP, RDP, and others that might be accidentally open to the public internet.
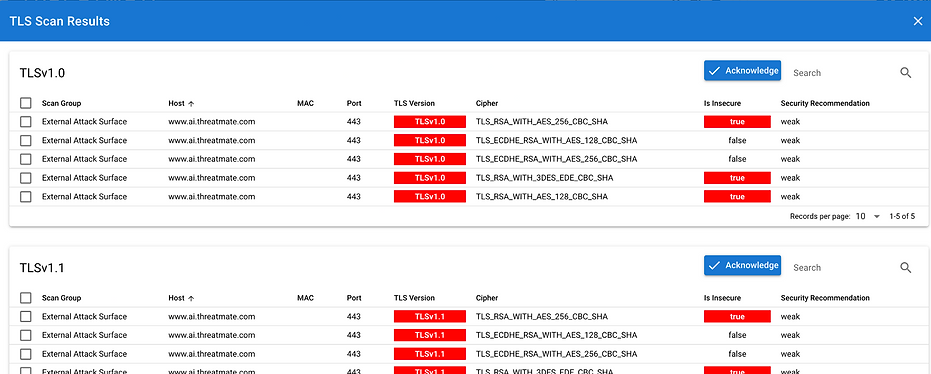
Thorough TLS Evaluations
Checks for outdated TLS versions, weak ciphers, and expired certificates to maintain robust encryption standards.
Internal Vulnerability Management Highlights
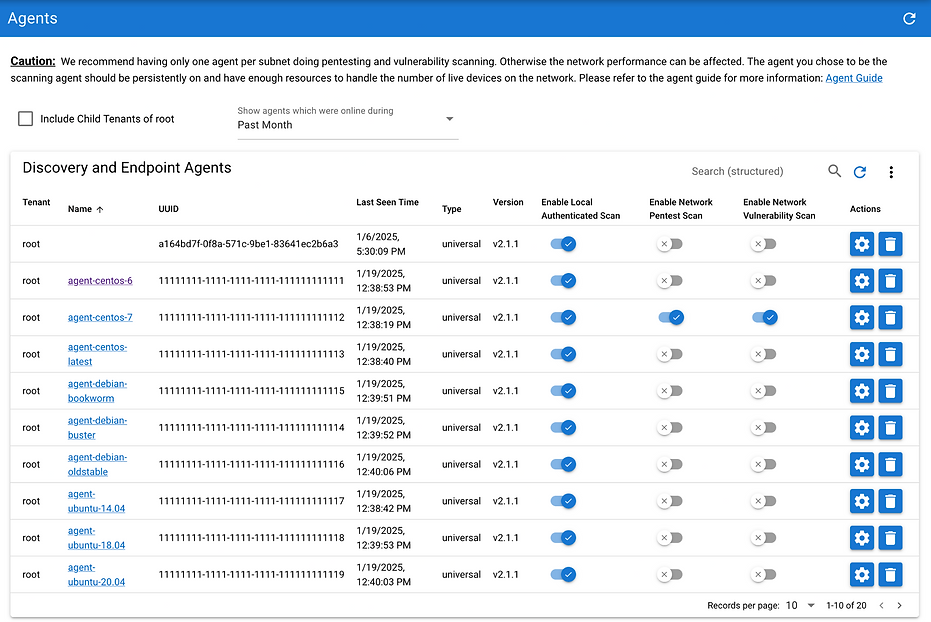
Complete Asset Discovery
The Unified Agent catalogs 100% of live devices on your internal network, eliminating hidden endpoints.
Twice-a-Day Scans
Automatic checks every 12 hours ensure you quickly detect new vulnerabilities from patches gone wrong, newly installed software, or reconnected devices.
Local & Network-Level Insight
Both local authenticated scans and network-based tests help you assess overall device health and configuration.
Why Continuous Vulnerability Management Matters
Ongoing Protection
Threats evolve daily—our frequent scanning schedule and updated definitions keep you one step ahead.
Prioritized Remediation
Combining CVSS severity with EPSS exploit likelihood ensures that critical, high-exploit issues are tackled first.
Risk Reduction
By identifying exposures at the moment they appear, you can address them before they lead to security incidents.
Peace of Mind
An automated process frees your security team from manual scans, letting them focus on higher-level tasks.